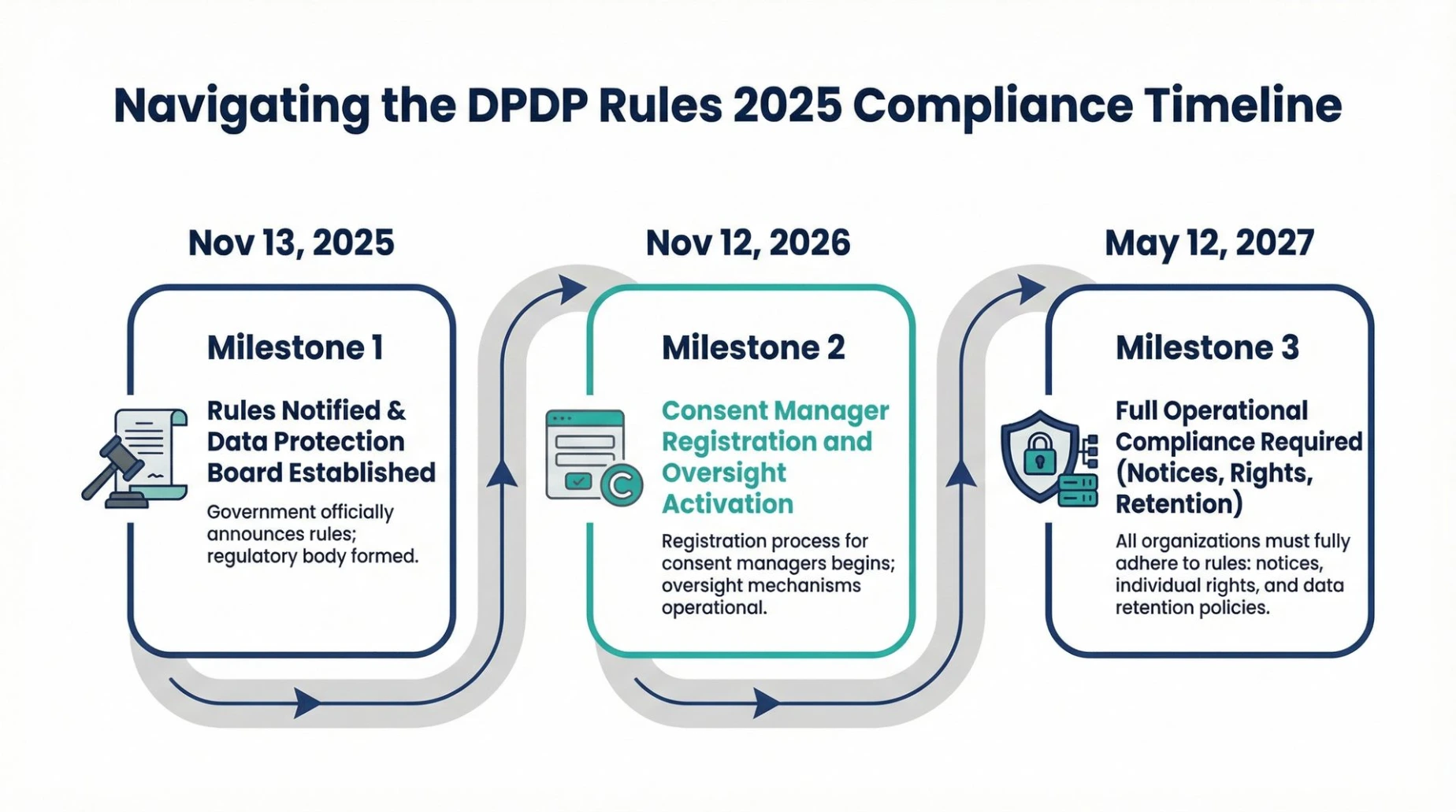
The landscape for independent professionals in India is undergoing a fundamental structural shift that moves beyond the simple exchange of services for fees. On November 13, 2025, the Ministry of Electronics and Information Technology (MeitY) notified the Digital Personal Data Protection (DPDP) Rules, 2025, effectively ending the period of regulatory ambiguity that had persisted since the passage of the parent Act in 2023.1 This notification signifies the full operationalization of a framework that repositions the individual freelancer from a mere service provider to a regulated Data Fiduciary, carrying legal liabilities that were previously reserved for large corporate entities.3
As the digital economy matures, the security protocols used by freelancers are moving from the theoretical confines of the laboratory into necessary practical applications. The convergence of India's new data protection regime and the looming global shift toward post-quantum cryptography creates a complex environment where technical literacy is as vital as professional skill.5 For the millions of freelancers operating across graphic design, software development, content creation, and consulting, the message is clear: the era of informal data handling is over, and the era of cryptographic accountability has begun.7
The following analysis explores the intricate details of the DPDP Rules 2025, the technical transition toward quantum-resistant encryption, and the practical steps necessary for independent professionals to safeguard their livelihoods in this new regulatory epoch.

The Historical Evolution Toward Digital Accountability
The arrival of the DPDP Rules 2025 is the culmination of a decade-long journey toward digital sovereignty. The previous framework, largely based on the Information Technology Act of 2000 and the SPDI Rules of 2011, struggled to keep pace with the rapid proliferation of the gig economy and the complex data flows of modern SaaS applications.9 The current framework is built on the "SARAL" approach—Simple, Accessible, Rational, and Actionable—utilizing plain language to ensure that even small-scale operators can understand their obligations without needing a permanent legal team.3
The drafting of these rules was not a closed-door exercise. MeitY engaged in a nationwide consultation process, receiving 6,915 inputs from a diverse array of stakeholders, including startups, MSMEs, and civil society groups.3 This collaborative origin suggests that the rules are intended to be innovation-friendly while maintaining a strict focus on individual rights. However, for the freelancer, this "innovation-friendly" stance comes with the requirement of professionalizing every touchpoint where client data is handled.3
Under the new regime, the fundamental right to privacy is operationalized through seven core principles: consent and transparency, purpose limitation, data minimization, accuracy, storage limitation, security safeguards, and accountability.3 Each of these principles dictates a specific set of behaviors that the freelancer must adopt to avoid the substantial penalties outlined in the Act.
Defining the Roles within the Freelance Ecosystem
The first step in compliance is identifying one's role within the data lifecycle. The DPDP framework utilizes specific categories to assign liability and duty. For most freelancers, the primary roles will oscillate between being a Data Fiduciary and a Data Processor, depending on the specific contract and the level of control exercised over the data.4
| Term | Statutory Definition | Practical Application for Freelancers |
| Data Principal | The individual to whom the personal data relates. 3 | The end-user of a client's app or a direct client themselves. |
| Data Fiduciary | An entity that determines the purpose and means of data processing. 3 | A freelancer who collects leads or manages their own customer database. |
| Data Processor | An entity that processes personal data on behalf of a Fiduciary. 3 | A developer who processes a client's user list according to instructions. |
| Significant Data Fiduciary (SDF) | Entities designated by government based on volume/risk. 2 | High-impact agencies or those handling sensitive biometric/financial data. |
The distinction is vital because Section 8(1) of the DPDP Act places the ultimate responsibility for compliance on the Data Fiduciary, regardless of whether the actual processing is outsourced to a third-party vendor or a sub-contractor.4 This means a freelancer acting as a Fiduciary cannot claim "it was the software's fault" if a breach occurs. Accountability is non-delegable.4
Detailed Analysis of the DPDP Rules 2025
The Rules provide the operational depth that the parent Act lacked. They turn broad statutory duties into auditable requirements that the Data Protection Board (DPBI) can test and enforce.8
Rule 3: The New Standard for Notice and Consent
The most visible change for freelancers will be how they obtain permission to handle data. Consent must now be an "auditable transaction".13 Blanket approvals or pre-ticked boxes are no longer valid. Every request for consent must be preceded or accompanied by a clear notice that is standalone and written in plain language.14
The notice must include an itemized description of the personal data being collected and the specific purpose for each category.13 For example, if a freelance digital marketer collects a client's phone number, the notice must specify if it is for "service updates" or "marketing via WhatsApp." Furthermore, the professional must provide a simple mechanism for the individual to withdraw their consent at any time, which must be as easy as the process of giving it.14
Rule 4: The Emergence of Consent Managers
A unique feature of the Indian framework is the introduction of Consent Managers. These are independent entities registered with MeitY that act as intermediaries, allowing individuals to manage their consents across multiple services from a single platform.2 These managers must be India-based, possess a minimum net worth of ₹2 crore, and provide an interoperable platform.2 For freelancers building digital products, integrating with these managers will become a standard technical requirement by late 2026.1
Rule 6: Reasonable Security Safeguards and the Mandate for Encryption
Perhaps the most technically demanding part of the new rules is the requirement for "reasonable security safeguards." While the Act provided a high-level mandate, the Rules explicitly suggest the adoption of encryption, masking, and tokenization to prevent unauthorized access or disclosure.13
Data Fiduciaries are now required to maintain processing logs and traffic data for at least one year.1 This means a freelancer must have a system that tracks who accessed the data, when, and from where. These logs are critical for detection, investigation, and remediation in the event of a breach.13 The rules also emphasize the need for "business resilience," requiring professionals to have data backups to ensure continued processing if the integrity of the primary data is compromised.15
Rule 7: The 72-Hour Breach Notification Window
The era of keeping data breaches quiet is over. Under Rule 7, if a freelancer becomes aware of a personal data breach, they have a dual obligation. First, they must intimate the affected individuals without delay, using plain language to describe the breach and the steps they can take to protect themselves.13 Second, they must provide a detailed report to the Data Protection Board within 72 hours of discovery.2 This report must include the nature of the breach, the categories of data compromised, and the remedial actions taken.15
Transitioning Encryption: From the Laboratory to Practical Application
While the legal framework sets the requirements, the technological landscape is shifting beneath the feet of every digital professional. The core of "reasonable security" is encryption, but the types of encryption that were sufficient yesterday are facing an existential threat from the rise of quantum computing.5
The Traditional Standard: AES-256 and RSA
Currently, most freelancers rely on symmetric encryption like AES-256 for data at rest and asymmetric encryption like RSA or ECC for data in transit (such as SSL/TLS for websites).22 These methods are based on mathematical problems that are computationally impossible for today's classical computers to solve.21 However, the transition to practical application now requires moving beyond simple implementation to "crypto-agility"—the ability to update these algorithms as threats evolve.6
The Quantum Threat: Why 2026 is the Turning Point
A "cryptographically relevant quantum computer" (CRQC) is a system powerful enough to break current public-key cryptography using Shor's algorithm.22 While widespread quantum availability is estimated for the 2030s, the threat of "Harvest Now, Decrypt Later" is already a reality.21 In this scenario, threat actors intercept and store encrypted data today, intending to decrypt it once they have access to quantum machines.21
For freelancers handling sensitive client contracts, intellectual property, or long-term financial records, 2026 is viewed as a critical year for adopting post-quantum cryptography (PQC).6 Regulatory mandates are expected to tighten around the requirement for quantum-resistant standards to ensure the long-term confidentiality of archived data.6
NIST Standards and New Algorithms
The global effort to standardize PQC is being led by organizations like the U.S. National Institute of Standards and Technology (NIST), which has already identified primary candidates for transition.
| Algorithm Category | Leading Standard | Practical Application |
| General Encryption | CRYSTALS-Kyber | Securing data at rest and exchanges over public networks. 21 |
| Digital Signatures | CRYSTALS-Dilithium | Authenticating identity and ensuring document integrity. 23 |
| Signature Alternatives | SPHINCS+ | Used when high levels of security are needed over smaller signature sizes. 25 |
Freelancers in 2026 will need to seek out "hybrid cryptography" solutions that combine classical algorithms with these post-quantum ones.6 This ensures backward compatibility while providing a layer of defense against emerging quantum threats.6
The Economic Impact on the Freelance Market
The move from informal to regulated data handling is not without cost. Experts suggest that Indian enterprises, including MSMEs and large agencies, will see a 10-30% increase in spending for IT, cybersecurity, and data governance.26

Budgeting for Compliance
For a solo freelancer or a small agency, the financial burden of the DPDP transition includes several key areas. Legal and operational overhauls, even on a small scale, can range from ₹20 lakh to ₹75 lakh for mid-market entities, but individual professionals can manage these costs by utilizing standardized tools and platforms.26
| Compliance Activity | Estimated Cost Range (Professional Scale) | Frequency |
| Legal Audit/DPA Drafting | ₹10,000 - ₹40,000 | Once/Updates 26 |
| Encryption/PQC Software | $1 - $15 per month | Ongoing 27 |
| Consent Management Tools | ₹15,000 - ₹50,000 | Implementation 26 |
| Training/Upskilling | ₹2,000 - ₹5,000 | Annual 9 |
Beyond direct costs, there is a "revenue disruption" phase expected between 2025 and 2027. Behavioral-dependent marketing segments could see a 10-25% decline in revenue as brands pause campaigns to audit data and collect fresh, compliant consent.26 However, the long-term outcome is a higher-trust ecosystem where conversion quality and signal density are improved.26
The Danger of the "Lazy Tax"
Compliance is now a "strongest financial defense".7 Failing to delete ex-customer data or keeping "dormant records" creates an exposed liability.7 If a breach occurs on data that should have been deleted according to the purpose limitation principle, the resulting penalty from the DPBI will likely be far higher than if the data had been actively managed.7 Data discovery—knowing exactly what is being hoarded—is no longer optional; it is a statutory necessity.7
Practical Implementation: A Guide for the Indian Freelancer
Transitioning to this new era requires a systematic approach that blends legal awareness with technical upgrades. The following steps provide a roadmap for the 2026-2027 compliance window.
Step 1: Data Discovery and Mapping
A professional cannot protect what they do not know they have. Freelancers must conduct an inventory of all systems, data stores, and third-party vendors touching personal data.14 This involves listing every touchpoint in the customer journey where data is collected—from lead forms to WhatsApp groups.18 A visual "Record of Processing Activities" (RoPA) diagram should be prepared to track the flow of data inside and outside India.18
Step 2: Redesigning UI/UX for Consent
By mid-2026, freelancers must have standardized consent language integrated into their platforms. This includes creating a "Privacy Center" or a dashboard where clients and users can exercise their rights to access, correct, or erase their data.8 The interface must clearly separate consent from other terms and conditions, avoiding the use of "dark patterns" that manipulate users into giving permission.8
Step 3: Upgrading the Security Stack
Transitioning encryption to practical application means moving to tools that support the new DPDP mandates.
Encryption at Rest: Ensure all professional devices use full-disk encryption (like FileVault or BitLocker). For individual file security, tools like AxCrypt or Xecrets Ez offer powerful, affordable encryption for local folders.27
Encrypted Cloud Storage: Shift to providers like Proton Drive or NordLocker, which offer end-to-end encryption with zero-knowledge protocols.27
Endpoint Protection: Use tools like DriveStrike for remote wipe and remote lock capabilities, ensuring that if a laptop or phone is lost, the data remains inaccessible.28
Logging and Monitoring: Implement solutions that maintain access logs for at least one year, as required by Rule 6 and Rule 8.1
Step 4: Updating Contracts and Vendor Management
The "Vendor Excuse" no longer works.7 Freelancers must review their agreements with clients and sub-contractors to include specific DPDP obligations.7 These contracts must outline purpose limitation, security safeguards, breach reporting timelines, and the right to audit the processor's compliance.4 For cross-border transfers, freelancers must ensure they are using "Standard Contractual Clauses" (SCCs) and transferring data only to government-approved countries.31
Step 5: Managing the Children's Data Constraint
If a freelancer's work involves children (under 18), the rules are even stricter. Rule 10 mandates "verifiable parental consent" before any data processing can occur.14 This may involve identity checks using government-authorized sources like DigiLocker or virtual tokens.18 Targeted advertising and behavioral profiling of minors are explicitly prohibited.12
Reconciling Privacy Rules with Income Tax Obligations
A significant point of conflict for Indian freelancers is the mismatch between the DPDP Act and the Income Tax Act.4 While the DPDP Rules advocate for data erasure once the purpose is fulfilled (with a minimum of one year), tax laws require the preservation of records for six to ten years.4
In this scenario, the professional must act as a "Data Trustee." They must reconcile these obligations by actively mapping and documenting the "legal basis" for retaining each category of data.4 Data required for statutory tax audits is exempt from immediate erasure but must still be secured with the same high level of encryption and access control as active data.4 The key is to segregate "business notes" and "marketing cookies" (which must be deleted) from "invoices" and "payment records" (which must be archived).4
The Penalties and the Data Protection Board
The Data Protection Board of India (DPBI) functions as an independent body overseeing compliance and inquiring into breaches.3 For the freelancer, the Board is the primary regulator. If a Principal feels their rights have been violated, they can approach the Board for redressal after a 90-day grievance period with the fiduciary.13
The penalty structure is designed to be substantial enough to deter negligence.
| Type of Breach | Maximum Penalty |
Failure to implement security safeguards 3 | ₹250 Crore |
Violation involving children's data 3 | ₹200 Crore |
Delayed or missing breach notification 3 | ₹200 Crore |
General violation of the Act or Rules 3 | ₹50 Crore |
While these figures represent maximums, the board evaluates the "scale of harm" and the "nature of the violation" when determining the final fine.31 For an individual professional, even a ₹5 lakh penalty could be life-changing, emphasizing the need for proactive innovation rather than reactive damage control.6
The Role of Significant Data Fiduciaries (SDFs)
While most freelancers will fall into the standard Data Fiduciary category, those who handle massive volumes of data or high-risk categories may be designated as Significant Data Fiduciaries by the government.2 These entities face a much higher compliance bar, including:
Appointment of a dedicated Data Protection Officer (DPO) based in India.12
Mandatory annual independent data protection audits.2
Periodic Data Protection Impact Assessments (DPIAs) to evaluate the risks of new technologies or algorithmic processing.1
For most solo professionals, the goal is to remain below this threshold by practicing "data minimization"—collecting only what is absolutely necessary and deleting it promptly.7
Future Outlook: The Path to 2027 and Beyond
The 18-month countdown that began in late 2025 will define the next decade of the Indian digital economy.1 By May 2027, the grace period for "we are working on it" will have vanished.1 Freelancers will be expected to demonstrate "Phase 3-level maturity," meaning their consent flows are automated, their breach response plans are simulated, and their encryption stacks are quantum-ready.1
The move toward a sovereign AI stack and indigenous foundation models in India will further complicate data privacy.41 Professionals will need to ensure that personal data is anonymized or pseudonymized before it is used in AI pipelines or for training local models.19 Algorithmic fairness and transparency will become part of the fiduciary duty, especially as AI-driven systems increasingly automate decision-making in sectors like recruitment and finance.17
Ultimately, the DPDP Rules 2025 transform the role of the freelancer into that of a "data custodian".4 This is a definitive economic shift. Those who embrace the transition of encryption from the laboratory to practical application will find themselves at a strategic advantage.6 They will not only meet their legal obligations but will foster the "digital trust" necessary to thrive in a global, privacy-conscious world.1
